Introduction
We are going to explain in this article how you can configure the incoming spam filter of SpamExperts in Plesk.
Prerequisites
- A VPS, Budget Dedicated Server or Dedicated Server running Plesk control panel
- SpamExperts as an incoming spam filter
Step 1: Log in to Plesk
Log in to your Plesk environment via https://plesk.hosted-by-snel.com:8443.
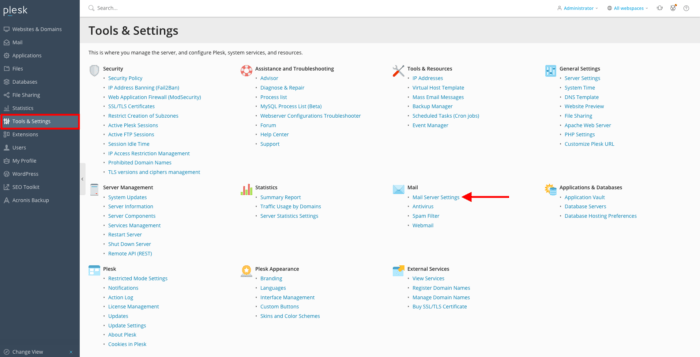
Step 2: Mail Server Settings
On the left pane, click Tools and Settings. View tab Mail and open the mail server settings by clicking to Mail Server Settings.
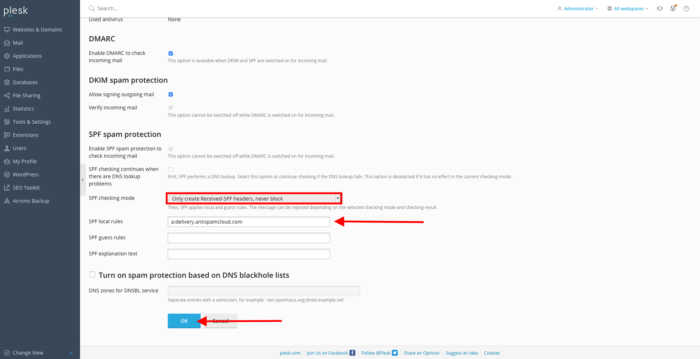
Step 3: SPF Spam Protection
Scroll down to the section SPF spam protection. The Plesk default configuration is set to do an SPF check but it will never block the mail regardless of the outcome of the SPF check. Based on your mail server configuration, it can decide to put it in the spam box or not.
In our environment, we are using SpamExperts as incoming spam filters. They advise whitelisting their mail servers, this will prevent Plesk from rejecting deliveries from their mail servers. Enter the following text a:delivery.antispamcloud.com in the SPF local rules.
Save your changes by clicking OK.
Step 4: SpamAssassin
If SpamAssassin is not enabled for your server go further to step 5. Use SSH to log in. Open /etc/mail/spamassassin/local.cf and append the following line.
trusted_networks 5.79.65.71/32 5.79.65.85/32 5.79.65.86/32 5.79.65.88/32 5.79.72.138/31 5.79.86.40/31 5.79.86.42/32 7.48.65.165/32 31.204.150.41/32 31.204.154.86/32 31.204.154.235/32 31.204.154.236/31 31.204.154.238/32 31.204.155.103/32 31.204.155.105/32 31.204.155.116/32 37.48.65.165/32 38.89.254.32/32 38.89.254.34/32 38.89.254.36/32 38.89.254.38/32 38.89.254.79/32 38.89.254.80/31 38.89.254.82/32 38.89.254.150/31 38.89.254.152/29 38.89.254.160/30 38.89.254.164/32 38.101.250.82/31 38.107.142.88/30 38.107.142.92/32 38.109.53.17/32 38.109.53.19/32 38.109.53.21/32 38.109.53.35/32 38.109.53.36/32 38.109.53.38/31 38.109.53.40/32 38.111.198.182/31 38.111.198.184/30 38.111.198.188/31 38.128.97.251/32 38.128.97.252/31 38.128.97.254/32 46.165.209.5/32 46.165.209.232/32 46.165.217.141/32 46.165.217.142/32 46.165.222.180/32 46.165.223.3/32 46.165.223.16/32 46.165.224.87/32 46.165.232.196/31 62.212.72.235/32 69.64.57.52/32 69.64.57.56/32 69.64.57.60/31 78.46.59.153/32 81.17.56.93/32 81.17.56.160/32 81.17.62.140/31 81.17.62.142/32 81.17.62.145/32 81.171.15.183/32 82.192.64.142/32 82.192.64.145/32 85.17.23.2/32 85.17.23.118/31 85.17.76.141/32 85.17.178.207/32 85.25.176.214/32 85.25.237.90/31 85.25.237.172/31 88.99.25.231/32 88.99.245.49/32 88.198.67.44/32 94.75.244.162/31 94.75.244.176/32 94.130.134.223/32 94.130.134.226/32 94.130.139.116/32 94.130.140.62/32 94.130.238.210/32 95.211.100.171/32 95.211.100.172/31 95.211.121.203/32 95.211.160.147/32 95.211.233.204/32 95.211.233.206/32 95.216.33.117/32 95.216.33.118/32 95.216.36.251/32 95.216.36.252/32 95.216.37.109/32 95.216.37.110/31 95.216.37.113/32 108.59.11.79/32 130.117.54.78/31 130.117.54.80/30 130.117.54.84/31 130.117.249.135/32 130.117.249.136/31 130.117.249.138/32 130.117.249.148/30 130.117.251.26/31 130.117.251.35/32 130.117.251.36/30 130.117.251.40/31 130.117.251.42/32 130.117.251.44/31 138.201.61.103/32 138.201.61.104/32 138.201.61.135/32 138.201.61.138/32 138.201.61.140/32 138.201.61.142/32 138.201.65.23/32 138.201.138.133/32 138.201.140.156/32 138.201.141.136/32 138.201.192.37/32 138.201.192.38/32 149.5.26.35/32 149.5.26.36/30 149.5.26.40/31 149.5.26.42/32 149.5.95.71/32 149.5.95.72/30 149.5.95.76/31 149.5.95.78/32 149.12.33.20/30 149.12.33.24/30 149.13.73.45/32 149.13.73.46/31 149.13.73.48/32 149.13.73.55/32 149.13.73.56/31 149.13.73.58/32 149.13.73.60/32 149.13.75.38/31 149.13.75.42/31 149.13.75.45/32 149.13.75.46/32 154.61.81.53/32 154.61.81.54/32 154.61.81.57/32 154.61.81.58/32 154.61.81.199/32 154.61.81.200/31 154.61.81.202/32 154.61.135.19/32 154.61.135.20/31 154.61.135.22/32 154.61.135.25/32 154.61.135.26/32 162.210.192.149/32 162.210.193.232/32 162.210.198.115/32 162.210.198.139/32 178.63.55.124/32 185.201.16.200/31 185.201.17.200/31 185.201.18.200/31 185.201.19.200/31 188.138.56.27/32 188.138.56.29/32 188.138.125.29/32 192.69.16.127/32 192.69.16.130/32 195.201.61.177/32 198.7.58.151/32 198.7.58.152/30 199.115.113.161/32 199.115.114.223/32 199.115.117.1/32 199.115.117.7/32 207.244.83.249/32 209.58.136.65/32 209.58.183.202/32 209.126.110.250/31 209.126.122.18/32 212.7.192.86/32 212.32.233.198/32 212.32.243.83/32 212.32.246.15/32 217.20.113.37/32 217.118.19.158/32 220.233.31.56/30 220.233.31.61/32
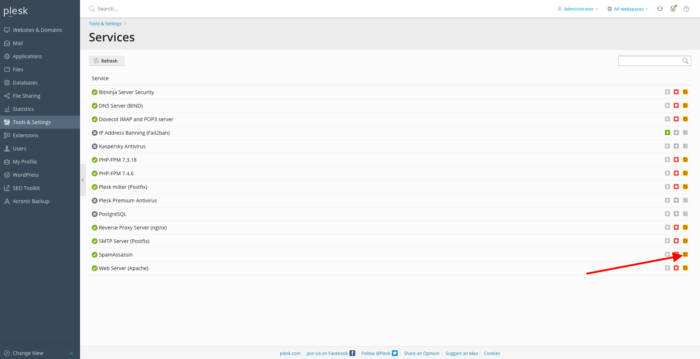
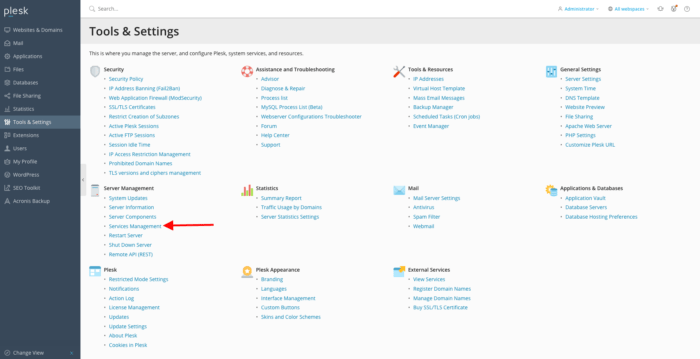
After adding mail servers as trusted, we can restart SpamAssassin. Go back to Plesk. On the left pane of the dashboard, click Tools and Settings . Look at the tab Server Management and open service management by clicking to Services Management.
Restart SpamAssasin by clicking the restart icon.
Step 5: Test Email delivery
In this step, it is advised using a domain that is not using SpamExperts for incoming or outgoing emails. Send a test email to a user that is hosted on the Plesk server which you are configuring.
Once the mail is received, open the mail headers.
Return-Path: <[email protected]> X-Original-To: [email protected] Delivered-To: [email protected] Received: from out7.antispamcloud.com (out7.antispamcloud.com [94.75.244.176]) by s19052020.hosted-by-snel.com (Postfix) with ESMTPS id 8A00A300683 for <[email protected]>; Tue, 19 May 2020 11:59:19 +0200 (CEST) Authentication-Results: s19052020.hosted-by-snel.com; dmarc=none (p=NONE sp=NONE) smtp.from=hosted-by-snel.com header.from=hosted-by-snel.com; dkim=pass header.d=hosted-by-snel.com.20150623.gappssmtp.com; spf=pass (sender IP is 94.75.244.176) [email protected] smtp.helo=out7.antispamcloud.com Received-SPF: pass (s19052020.hosted-by-snel.com: domain of hosted-by-snel.com designates 94.75.244.176 as permitted sender) client-ip=94.75.244.176; [email protected]; helo=out7.antispamcloud.com; Received: from mail-qv1-f46.google.com ([209.85.219.46]) by mx19.antispamcloud.com with esmtps (TLSv1.2:ECDHE-RSA-AES128-GCM-SHA256:128) (Exim 4.92) (envelope-from <[email protected]>) id 1jaz1c-0007jj-6d for [email protected]; Tue, 19 May 2020 11:59:16 +0200 Received: by mail-qv1-f46.google.com with SMTP id r3so6184368qve.1 for <[email protected]>; Tue, 19 May 2020 02:59:02 -0700 (PDT) DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=hosted-by-snel.com.20150623.gappssmtp.com; s=20150623; h=mime-version:from:date:message-id:subject:to; <> X-Google-DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=1e100.net; s=20161025; h=x-gm-message-state:mime-version:from:date:message-id:subject:to; <> X-Gm-Message-State: <> X-Google-Smtp-Source: <> X-Received: by 2002:a0c:9e53:: with SMTP id <>; Tue, 19 May 2020 02:59:00 -0700 (PDT) MIME-Version: 1.0 From: John Doe <[email protected]> Date: Tue, 19 May 2020 11:58:49 +0200 Message-ID: <> Subject: SPF Check To: [email protected] Content-Type: multipart/alternative; boundary="000000000000299d8005a5fd54a0" Received-SPF: pass (mx19.antispamcloud.com: domain of hosted-by-snel.com designates 209.85.219.46 as permitted sender) client-ip=209.85.219.46; [email protected]; helo=mail-qv1-f46.google.com; X-SPF-Result: mx19.antispamcloud.com: domain of hosted-by-snel.com designates 209.85.219.46 as permitted sender Authentication-Results: antispamcloud.com; spf=pass smtp.mailfrom=<[email protected]; dkim=pass header.i=hosted-by-snel.com.20150623.gappssmtp.com X-Spampanel-Class: unsure X-Spampanel-Evidence: Combined (0.29) X-Recommended-Action: accept X-Filter-ID: <> X-Report-Abuse-To: [email protected]
In the example above, we can find two Received-SPF values. We start from bottom to top. In the first Received-SPF, you can see that the SPF has passed, which means that SpamExperts did an SPF check on the email that he received from [email protected] and that the mail server with IP address 209.85.160.180 is permitted to send emails for [email protected].
Received-SPF: pass (mx19.antispamcloud.com: domain of hosted-by-snel.com designates 209.85.219.46 as permitted sender) client-ip=209.85.219.46; [email protected]; helo=mail-qv1-f46.google.com;
Let’s proceed with the second Received-SPF value. This is the SPF check on the destination mail server, so in our case, it is the Plesk server.
Received-SPF: pass (s19052020.hosted-by-snel.com: domain of hosted-by-snel.com designates 94.75.244.176 as permitted sender) client-ip=94.75.244.176; [email protected]; helo=out7.antispamcloud.com;
If SpamAssassin is enabled on your server, be aware that SpamAssassin also checks the SPF record. The SPF must pass otherwise it can increase the SpamAssassin score for incoming emails. You will find extra SpamAssasins headers in the email headers. In the snippet below you can find the lines where the SPF check passes for SpamAssassin.
X-Spam-Status: No, score=2.4 required=7.0 tests=DKIM_SIGNED,DKIM_VALID,
DNS_FROM_AHBL_RHSBL,HTML_MESSAGE,RCVD_IN_DNSWL_NONE,RCVD_IN_MSPIKE_H3,
RCVD_IN_MSPIKE_WL,SPF_PASS autolearn=no autolearn_force=no version=3.4.0Conclusion
Congratulations, you now have configured incoming spam filters of SpamExperts on your Plesk server.



Leave a Reply