Introduction
In this tutorial, you will learn the procedure of TLS/SSL certificate installation on Apache webserver running on Centos 6. Once you are finished, all traffic between the server and client will be encrypted and safe. This is a standard practice of securing e-commerce websites and other financial services online.
Prerequisites
Before you begin working with this guide you’ll need these:
- SSH with Root user access to the CentOS 6 VPS
- The Apache web server with properly a domain and vhost configure
Step 1: Installing python and ssl dependencies
The thing about CentOS 6.x ( Centos 6.5, 6.6, 6.7 etc ) is, they come with Python 2.6 whereas Let’s Encrypt supports Python 2.7+ only. But, installing Python 2.7 in Centos 6.x is pretty simple. 🙂
Run the followings one after another after ssh root login to the centos 6 server:
yum install epel-release mod_ssl rpm -ivh https://rhel6.iuscommunity.org/ius-release.rpm yum --enablerepo=ius install git python27 python27-devel python27-pip python27- setuptools python27-virtualenv -y
[Please remember above 3 commands are only for CentOS 6 and 6.x distros.]
Step 2: Setting up Let’s Encrypt
We are going to use the Let’s Encrypt-auto wrapper script, which obtains some dependencies from the operating system and puts others in a python virtual environment. Now run this:
cd letsencrypt
git clone https://github.com/letsencrypt/letsencrypt
In a few time, you should be ready to proceed further and run the client.
Step 3: Running the Let’s Encrypt client
After the git clone is completed you can either just run lets’s encrypt auto or let’s encrypt, and the client will guide you through the process of obtaining and installing certs interactively or you can tell it exactly what you want it to do from the command line.
For example obtain a cert for your domain using the Apache plugin to both obtain and install the certs, you could do this:
./letsencrypt-auto --apache -d example.com -d www.example.com
Although you can use the Apache plugin to obtain and install the certs it didn’t work for me. I got an error: “The apache plugin is not working; there may be problems with your existing configuration.” This seems to be an issue with Apache 2.2 and until it’s fixed you can use the webroot authentication method as:
./letsencrypt-auto certonly --webroot -w /var/www/example/ -d example.com
Within a few times, the certificates will be created and available for actual use.
IMPORTANT! The first domain should be your base domain, in this sample it’s example.com
Step 4: Configure the SSL certificate(s)
In Let’s Encrypt configuration directory at “/etc/letsencrypt/live/the .pem files are as follows (from the Letsencrypt documentation):
privkey.pem: Private key for the certificate.
This must be kept secret at all times! Never share it with anyone, including Let’s Encrypt developers. You cannot put it into a safe, however – your server still needs to access this file in order for SSL/TLS to work.
cert.pem: Server certificate only. This is what Apache needs for SSLCertificateFile.
chain.pem: All certificates that need to be served by the browser excluding server certificates, i.e. root and intermediate certificates only. This is what Apache needs for SSLCertificateChainFile.
fullchain.pem: All certificates, including server certificate. This is a concatenation of chain.pem and cert.pem.
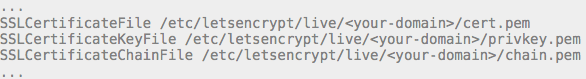
Now that we know which file is which we can configure our VirtualHost to use SSL with our new certs. Change the following lines in your Apache’s virtualhost’s SSL configuration:
Finally, restart apache and You can taste that your SSL is working.
Step 5: Setting up for the auto-renewal
Let’s Encrypt certificates are valid for 90 days only, but every web professionals will recommend you renew it within 75 days in order to avoid any issues. To accomplish this, get the autole.sh script from GitHub (https://github.com/damiadev/autole/) that automates tasks like:
Check the expiry date of the certificate and renew when the remaining days are below a value
Check that the directory for the challenge is well mapped
Alert the admin if it’s not possible to renew the certificate
Now you can renew certain domain’s certificates with:
./autole.sh --renew-all
To automate this renewal process you could setup a cronjob. First, you need copy this “autole.sh” into /usr/local/sbin/ and then open and edit the crontab by running:
crontab -e
This job can be safely scheduled to run every Monday at midnight:
0 0 * * 1 /usr/local/sbin/autole.sh --renew-all >> /var/log/sslrenew.log
The output of the script will be piped to /var/log/sslrenew.log file.
Conclusion
Congratulations, you have just secured your Apache web server by implementing the most anticipated security feature – free SSL certificates! From now on all traffic between your domain webserver and client is secure, you can be assured that no one could intercept the communication and alter or steal crucial information.



Great work guys. Much appreciated.
How can i do for the wildcard with this? Please guide.
Hey,
At the moment we do not have an article for issuing a wildcard. Your request is forwarded to our content writers.
`cd letsencrypt` – can't find this dir 🙁 unless you're referring to /etc/letsencrypt which isn't there either )
Maybe after I clone the certbot repo. Nope just 'downloaded' the files and nothing else happened after that.
This article might be deprecated. Recently we have been using acme.sh instead of certbot and have had great success with it. Unfortunately we have no public instructions on acme.sh yet except https://www.snel.com/support/securing-your-nginx-site-with-lets-encrypt-acme-sh/ but that article is for Debian 8 and Nginx.